Multifactor Authentication (MFA)
Set up MFA on your UA account
We strongly suggest that you set up BOTH the Authenticator App and email as a backup method in case you get a new phone.
Setup MFA with Authenticator App
To setup multiple MFA methods:
Step 1. Click on one of the "Setup" links above and follow the instructions.
Step 2. Go to https://mysignins.microsoft.com
Step 3. Click on "Add sign-in method"
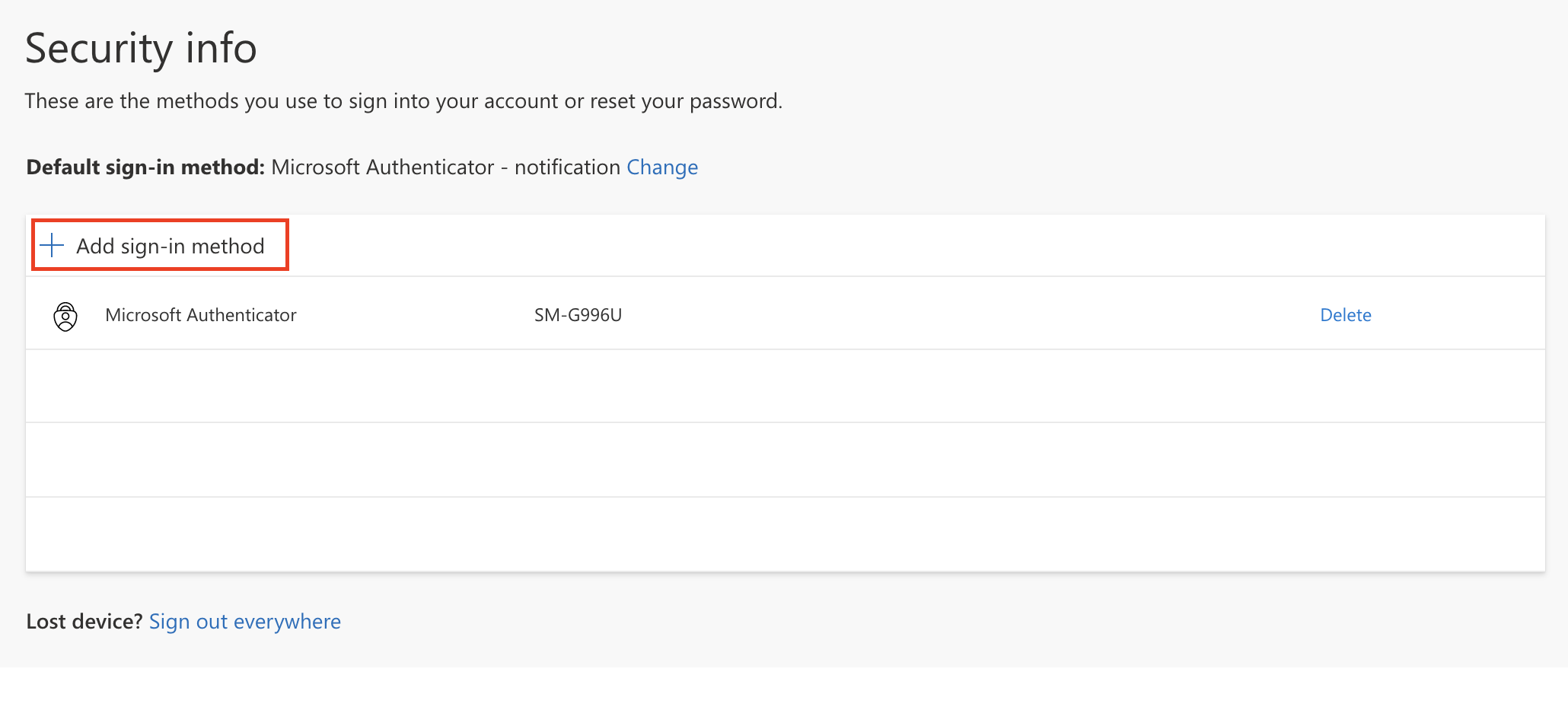
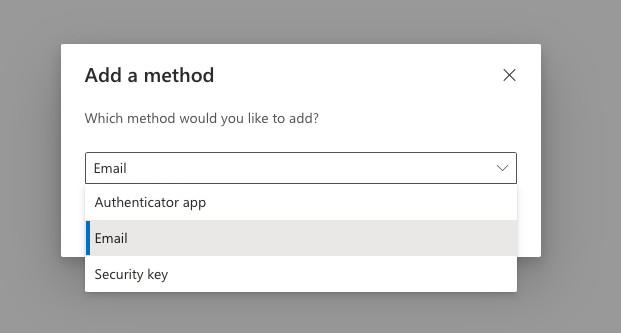
Step 4: Choose your additional method
FAQs
All faculty, staff, students, and university partners/contractors who receive a university account must use MFA.
Microsoft Authenticator (Preferred Method)
- Microsoft authenticator is the preferred solution for approving MFA requests. It provides simple push notifications so the user does not have to enter codes into the authentication dialogue, and can generate 6 digit TOTP codes if needed.
Phone Calls
- Users can register a cell or landline phone number to receive call that prompts them to approve the authentication.
Trusted devices and Locations
To make MFA rollout as smooth as possible, we have created two scenarios where your location or device will act as the additional authentication factor for MFA:
- Logins from on-campus will not receive an additional MFA challenge (satisfied with something you know and somewhere you are).
- Logins from University owned and managed machines will not require an MFA challenge (please contact security@uakron.edu to use this option).
Other Time-based One-time Password algorithm (TOTP) Authenticators
MFA works with any 3rd party authenticator that uses the TOTP protocol. This allows users to use an existing TOTP authenticator they may already have for their bank, personal email account, or video game service. While the University allows the use of third party applications as an MFA factor, we cannot provide support due to the variety of solutions out there.
- Mobile TOTP Applications: Authenticator apps such as Google Authenticator, Last Pass, DUO, and Authy are all compatible with Microsoft MFA. Several authenticator apps are also available for Android Wear and the Apple Watch.
- Desktop TOTP Applications: Desktop applications such as WinOTP Authenticator for Windows, Step Two for MacOS, and KeePassXC for Linux (and other platforms).
- Web Based TOTP Applications: Web services such as Authy can provide TOTP generation. Some of these web services also have companion apps for mobile and desktop devices.
- Hardware TOTP Tokens: Stand-alone TOTP authenticators are generally available and will work with Microsoft MFA. YubiKeys are also supported, though they require use of the Yubico Authenticator to generate TOTP codes.
You can update your authentication methods here.
Click on "Add Method" and add whichever method you wish.
If you still have your old phone, sign in here.
Click on "Add Method"
Choose "Authenticator App"
Follow the instructions.
If you do not have your old phone, contact the IT Service Desk at support@uakron.edu or 330-972-6888.
If a user is in need of special accommodation, please contact security@uakron.edu. We are happy to work with you to get your personal device or adaptive technology configured to seamlessly support MFA.
